In recent weeks, Syndis has observed a unique and targeted phishing campaign affecting over 4,000 travelers. Unlike traditional phishing waves that rely on mass emails and generic lures, this operation is precise, structured, and leverages real reservation data to deceive even security aware individuals based on what seems to be stolen or compromised data.
At the time of writing, we are actively investigating the scope of the targets since more victims are being identified. While it is unclear exactly when the underlying data was compromised, it is actively being weaponized. What makes this campaign particularly alarming is its ability to bypass standard security filters. Initial checks on platforms like VirusTotal showed zero immediate detections for the malicious URLs.
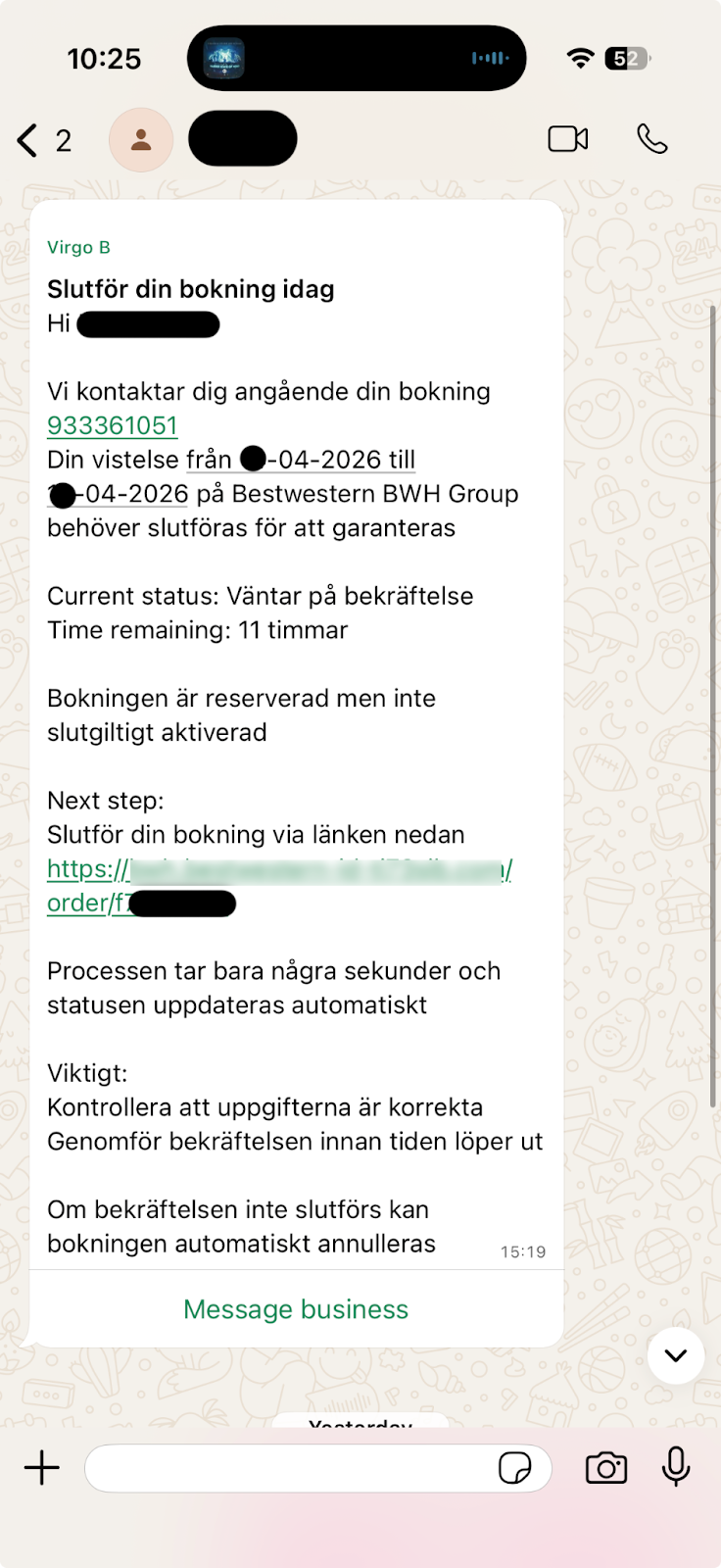
Victims are contacted directly via WhatsApp in their native language with messages referencing real hotel reservations, correct travel dates, and accurate payment amounts. The messages typically urge the recipient to confirm or complete a booking immediately to avoid cancellation. Because the details are correct, the urgency feels legitimate and that is exactly what the attackers are banking on.
The delivery vector: Why attackers are leveraging WhatsApp
Most phishing campaigns rely on email, but this threat actor has shifted to mobile messaging. WhatsApp provides several tactical advantages:
- Security Evasion: It represents a security gap, as most traditional security solutions lack the capability to block, alert on, or manage threats delivered via instant messaging apps like WhatsApp.
- Trusted Context & Lowered Scrutiny: A WhatsApp message feels more personal and immediate than an email, lowering victim skepticism. This is due to mobile-first behavior, where users are historically less likely to scrutinize URLs or verify sender details.
- High Engagement and Conversion: WhatsApp boasts high open rates and successfully bypasses the stringent filtering typical of enterprise email security gateways, directly contributing to high conversion rates for the attackers.
The delivery vector is strategic and intentional. The attackers are utilizing WhatsApp Business accounts, further increasing their perceived legitimacy.
Beyond brand spoofing: Ecosystem abuse
While early reporting connected this activity to Best Western themed messages, our technical indicators suggest the campaign is much broader.
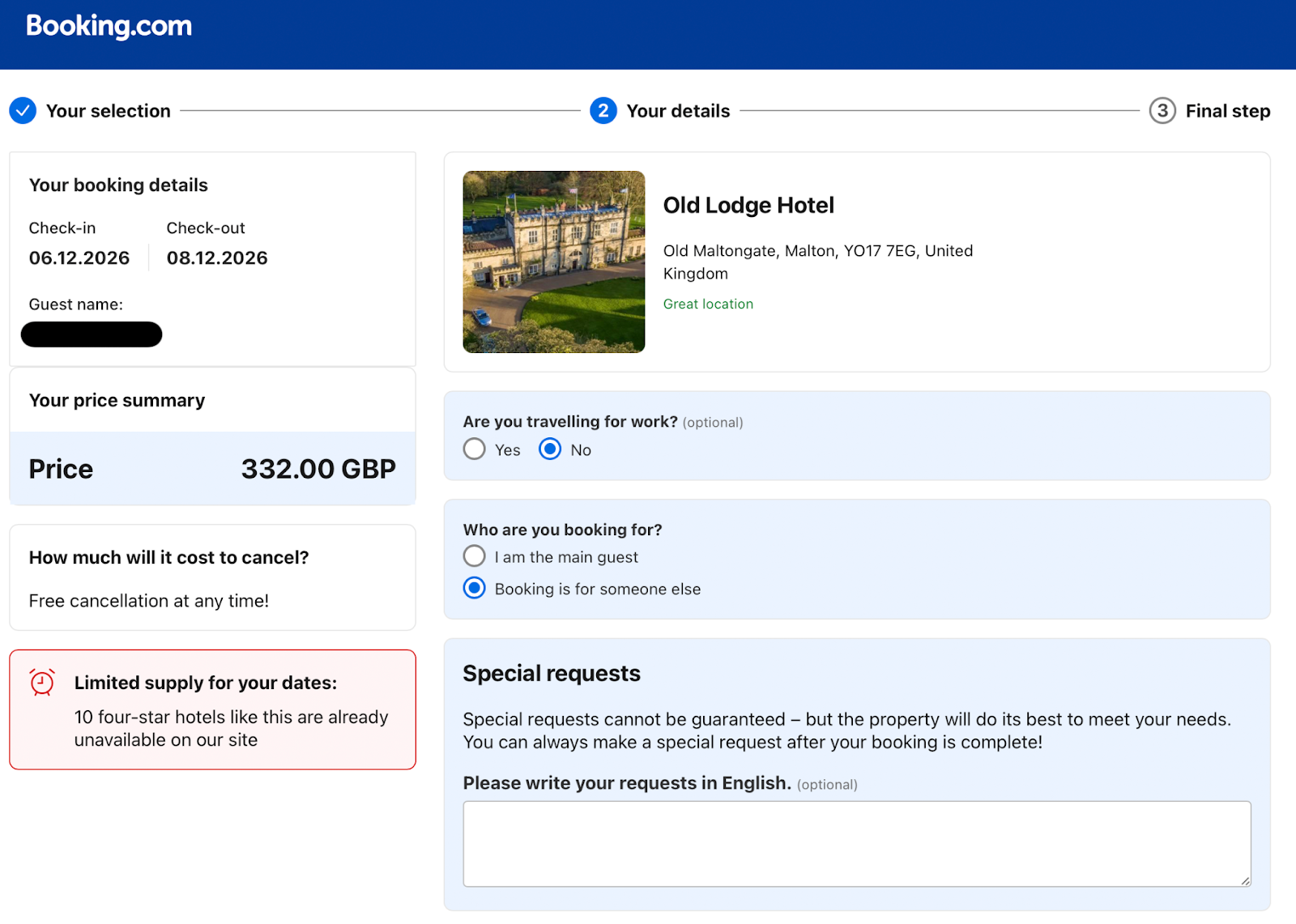
Evidence indicates that the same infrastructure and phishing templates are also targeting Booking.com reservations and potentially other major hospitality platforms. The attackers possess real reservation data likely obtained through partner compromise, credential theft, API abuse, or a third party breach. They are weaponizing this private data to increase their credibility and conversion rates.
Anatomy of an attack: Structured fraud infrastructure
One of the most revealing elements of this campaign is that each victim receives a unique URL. For example: hxxps://<URL>/order/f<UNIQUE ID>
The unique final path segment strongly suggests the presence of a backend database mapping a token to an individual booking record. This enables attackers to prefill correct payment amounts, track engagement, measure success rates, and disable URLs individually once reported. This is a mature, structured fraud operation.
Here is how the infrastructure likely operates:
- Data Acquisition: Attackers obtain reservation data (names, dates, hotel details, payment amounts) via upstream compromise.
- Token Generation: Each victim is assigned a unique identifier in a campaign control panel, linking the token to their booking details and contact information.
- WhatsApp Distribution: Personalized messages containing the victim-specific URLs are delivered.
- Dynamic Rendering: When a victim clicks the link, the server retrieves the associated booking details and dynamically renders a highly convincing, cloned confirmation page.
- Data Exfiltration: Payment card details are harvested and validated in real-time. Some kits even include simulated 3D Secure flows to maximize success rates.
Conclusion
This campaign demonstrates a worrying evolution of phishing into a precision fraud infrastructure. When attackers combine real data, trusted messaging platforms, and personalized delivery, their effectiveness skyrockets.
Organizations must operate under the assumption that exposed booking data can and will be weaponized, and strengthen their third-party risk and API controls accordingly. Travelers must remember to never trust urgent requests for payment via unsolicited messages, even if the details appear perfectly accurate. Always manage bookings directly through official websites or applications.
